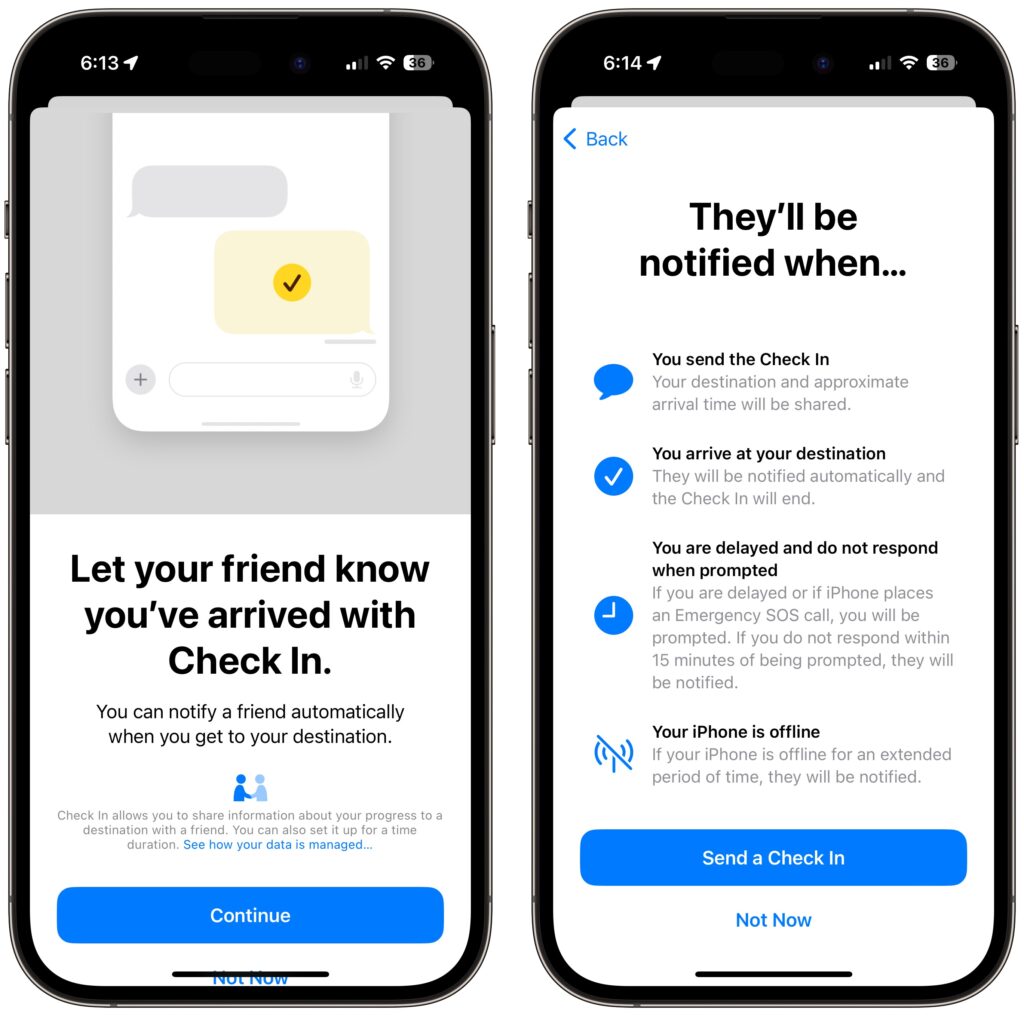
We’ve all had a friend or family member say, “Text me when you get home,” because they want the peace of mind from knowing you arrived safely. But what if something goes wrong—or you forget—so they never receive that text? They’ll be worried and won’t know where you are, if you’re OK, and so on.
In iOS 17, Apple has introduced the Check In feature to provide peace of mind—or in the worst case, to help emergency services. It’s conceptually simple. Before you leave to go somewhere, you create a Check In with someone—call them a safety partner—in Messages. You specify where you’re going and whether you’re driving, taking transit, or walking. Then, when you arrive, the Check In automatically ends, alerting your safety partner that you arrived. If you’re delayed en route, Check In takes that into account and extends the expected arrival time appropriately. If you fail to arrive, Check In shares your location and route with your safety partner. Also, if you make an Emergency SOS call or your iPhone or Apple Watch calls emergency services automatically during the Check In, it notifies your safety partner.
Not all situations revolve around following a specific route to a location, so Check In also supports timers. Perhaps a college student is going for an hour-long trail run and wants a friend to check on her if she’s not back as expected. She can use Check In to set a timer for 1 hour, share it with her friend, and when the timer ends, either tap the End button if she’s back or add more time if the run is going fine but taking longer than expected.
Although Check In may seem targeted at friends and family, it could have business uses as well. For instance, a destination Check In might work well for keeping tabs on a colleague traveling to a make-or-break pitch presentation.
Before you start using Check In with someone—in either direction—explain Check In to them and discuss an appropriate response if you or they fail to end Check In successfully. Responses should probably start with a quick text, followed by a phone call. If initial efforts to reach out are met with silence, contacting other people—friends, family members, neighbors, etc.—may be appropriate. At some point, depending on various factors, it will be time to call law enforcement. Of course, if the other person triggers an Emergency SOS during the Check In, call law enforcement immediately. At least in the US, if the person isn’t in your area, don’t call 911. Instead, find the law enforcement website for where the person is and call that organization’s 10-digit number. And here’s hoping it never comes to that!
Create a Check In
To get started with Check In, follow these steps:
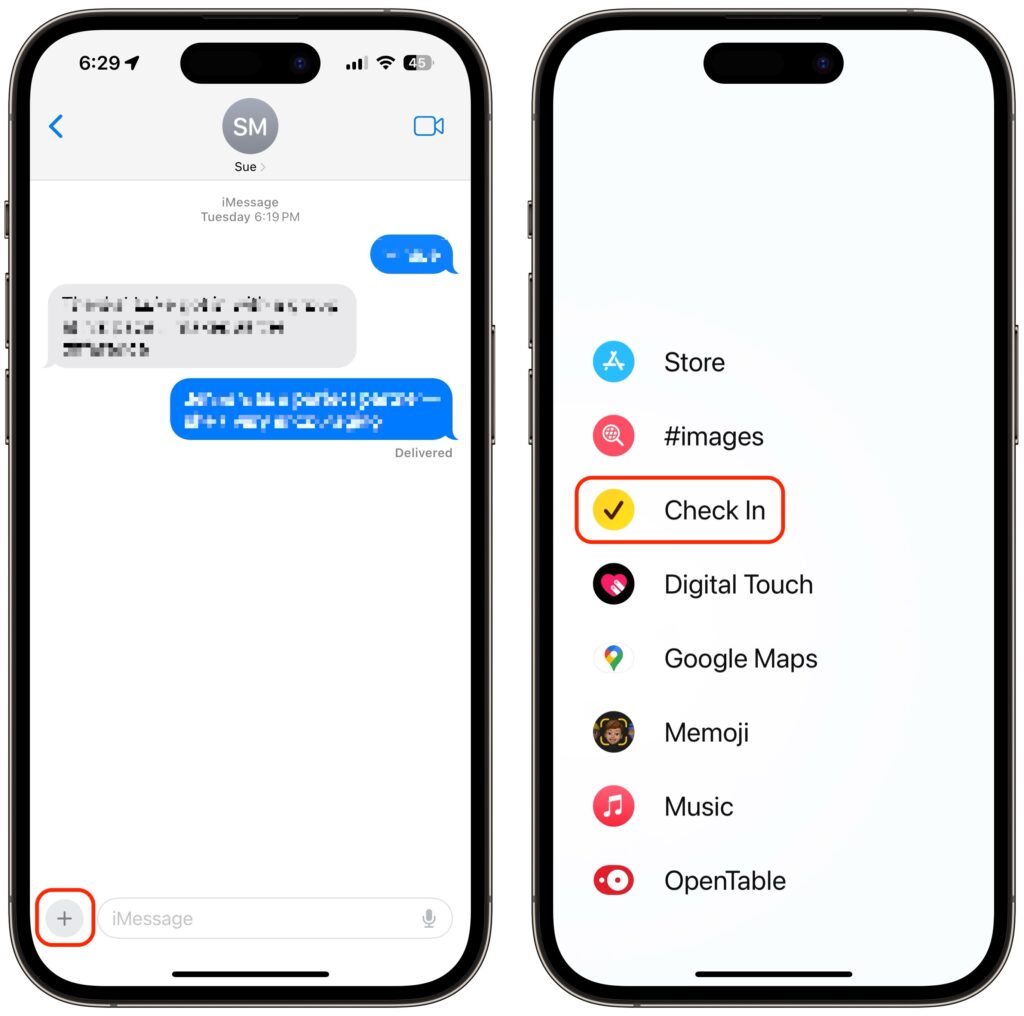
- In Messages, open a conversation with the person you want to be your safety partner (Check In doesn’t currently work with group conversations).
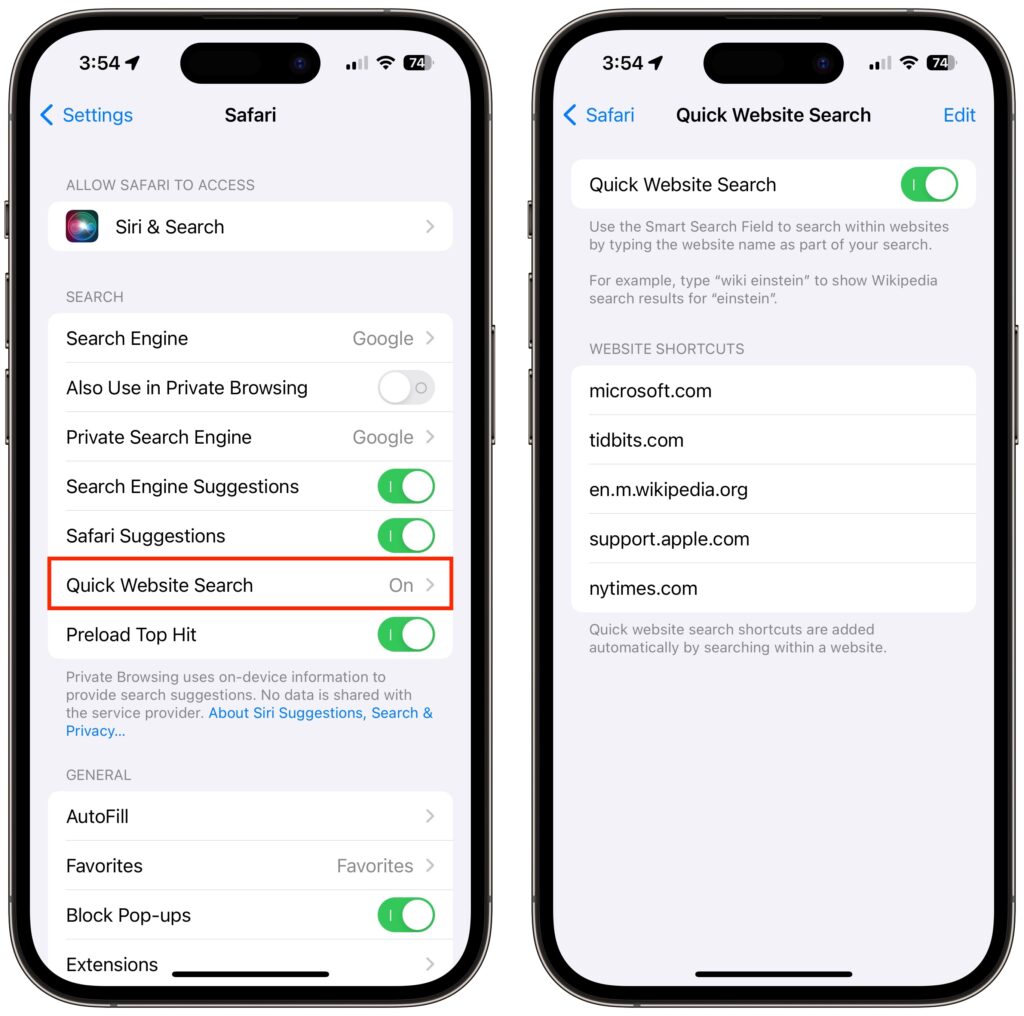
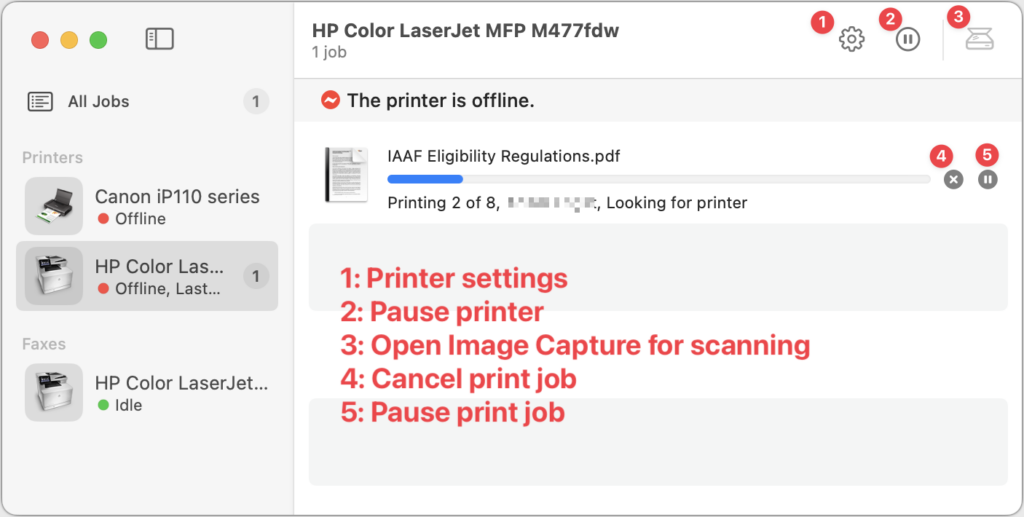
- Tap the ⊕ button to the left of the message field, tap More at the bottom, and tap Check In.
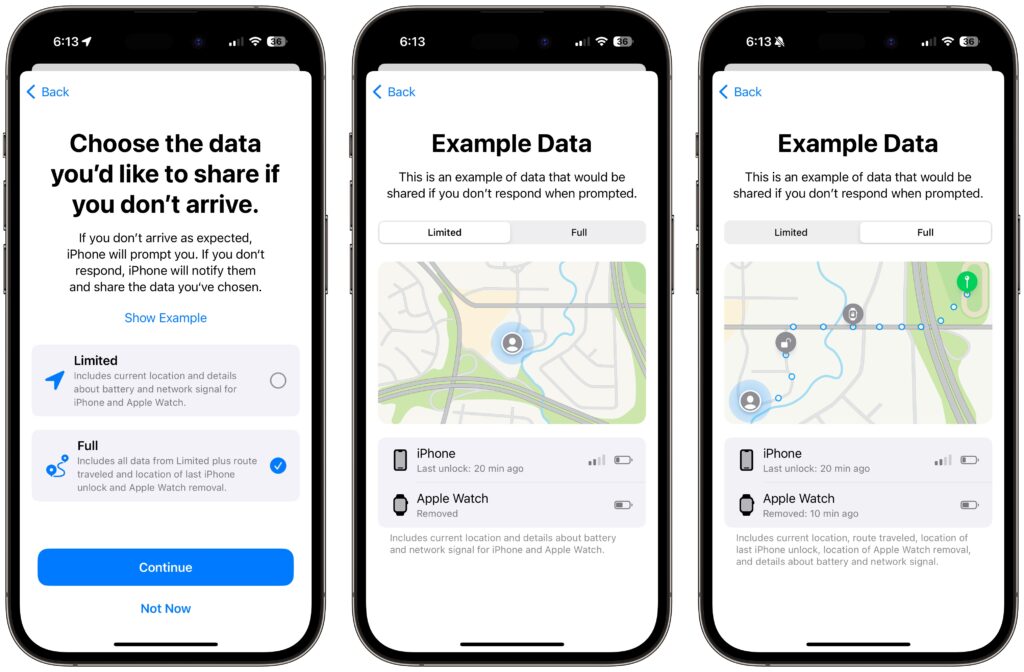
- The first time you invoke Check In, Messages walks you through a series of explanatory screens, one of which is important—the privacy level of the data shared with your safety partner if you don’t arrive. Select Full—we can see almost no reason why you wouldn’t want that person to be able to share your exact location and route with emergency services if something has gone wrong. (If necessary, tweak this setting later in Settings > Messages > Data.)
- On subsequent uses of Check In, an unsent card appears in the Messages conversation, usually set for an hour in the future. The card isn’t sent automatically so you can customize it before sending it.
- Tap the Edit button to adjust the timer or destination.
- To change the timer duration, use the time picker and tap Done. Skip to the last step in this list.
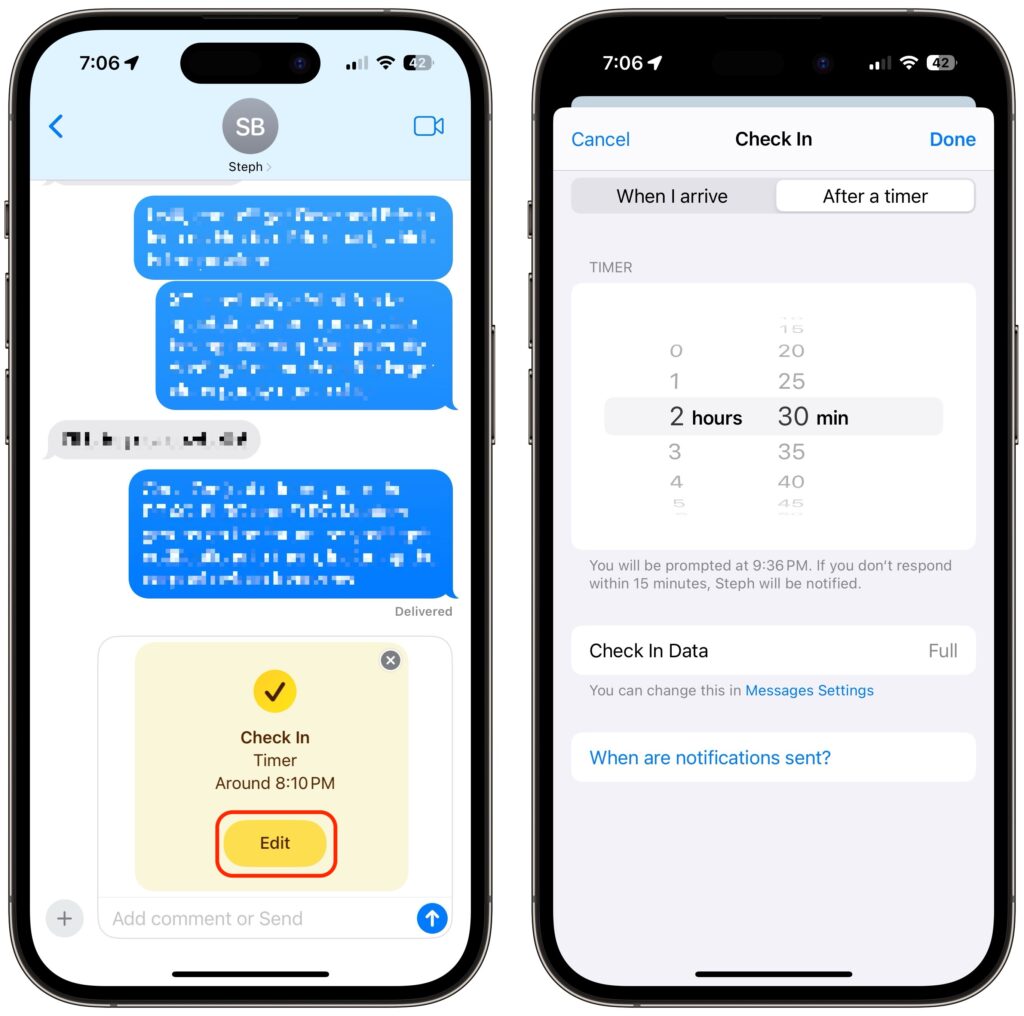
- To set a destination instead of a timer, tap “When I arrive” at the top of the screen.
- Tap the Change button, and in the map, either search for a location or find one manually by pinching and zooming—touch and hold the map to drop a destination pin. At the bottom of the screen, select Small, Medium, or Large to set the size of the area in which you’ll arrive.
- Tap Done to close the map and then select Driving, Transit, or Walking so Check In can estimate your arrival time based on your method of transportation.
- If you want additional buffer time, tap Add Time and give yourself 15, 30, or 60 minutes beyond when Check In thinks you’ll arrive. This shouldn’t usually be necessary.
- Tap Done.
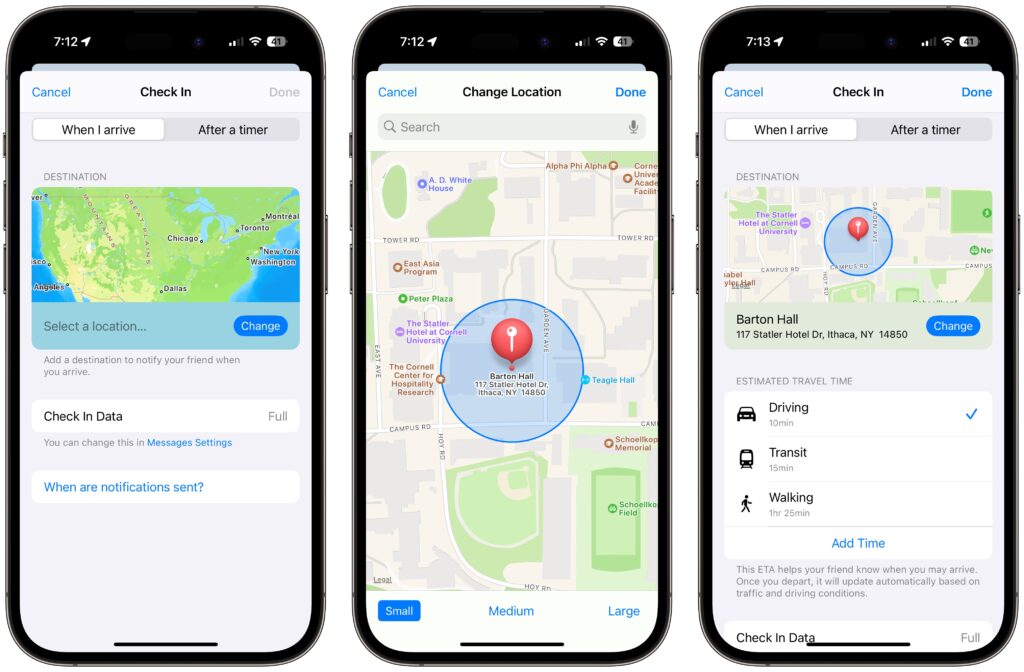
- Once you’re back to the Check In card in the Messages conversation, tap the Send button to start the Check In.
Note that safety partners can’t reject Check In cards.
End a Check In
Once you trigger a Check In, it can end in a few ways. First, you can cancel it before the timer completes or you arrive at your destination. Second, it can end successfully when you tap End when the timer finishes or when you arrive at your specified location. Third and finally, there’s the core purpose of the Check In, which is to alert your safety partner if you fail to respond to a timer or arrive where and when you said you would.
- Cancel: To cancel a Check In, tap the Details button on the Check In card in Messages, tap Cancel Check In, and agree that you don’t want your safety partner notified. Timer and destination Check Ins look slightly different but act the same way. Your safety partner will only see that the Check In card in Messages says it has ended.
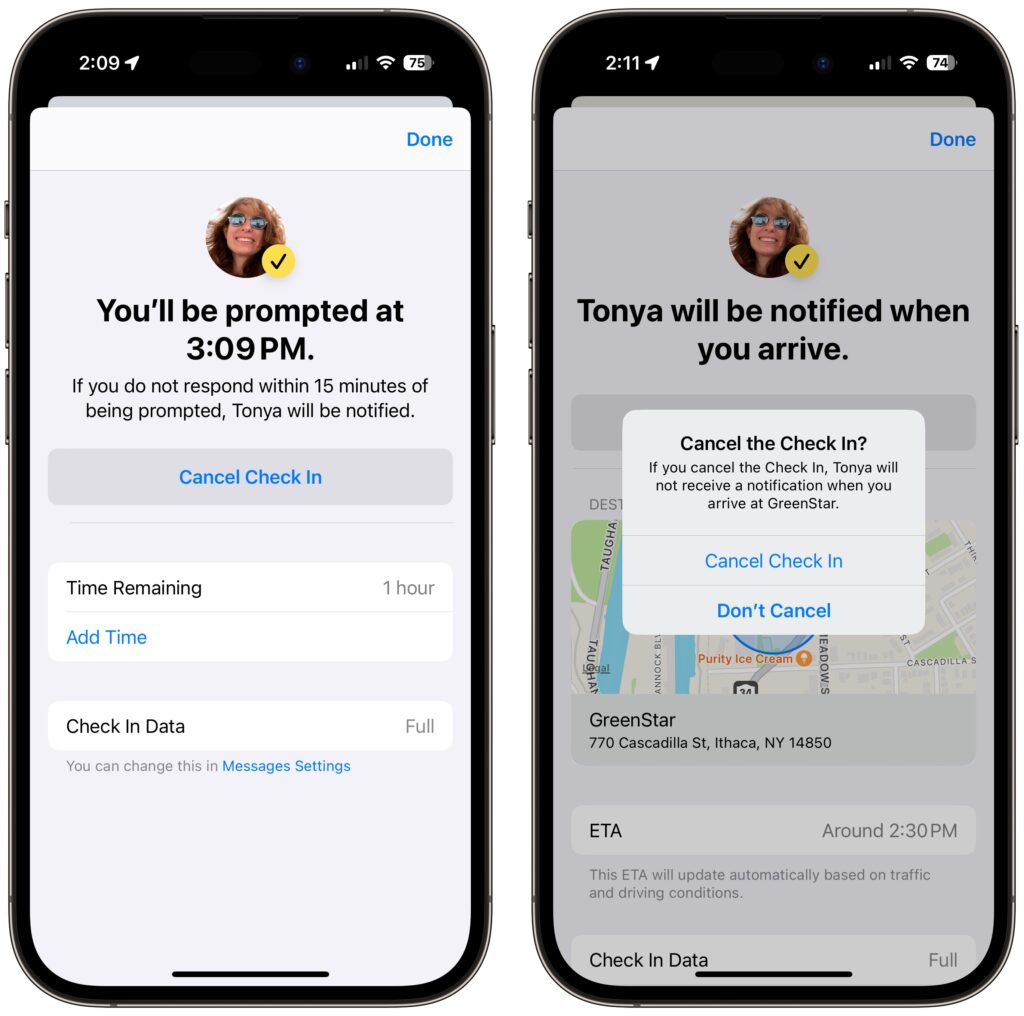
- End successfully: For a timer Check In to end successfully, you must respond when the iPhone prompts you (below left). All your safety partner sees when that happens is a note in the Check In card that the timer ended (below right). You don’t need to interact with your iPhone for a destination Check In to end successfully—just arrive at the specified location. The safety partner’s Check In card updates to say that you arrived.
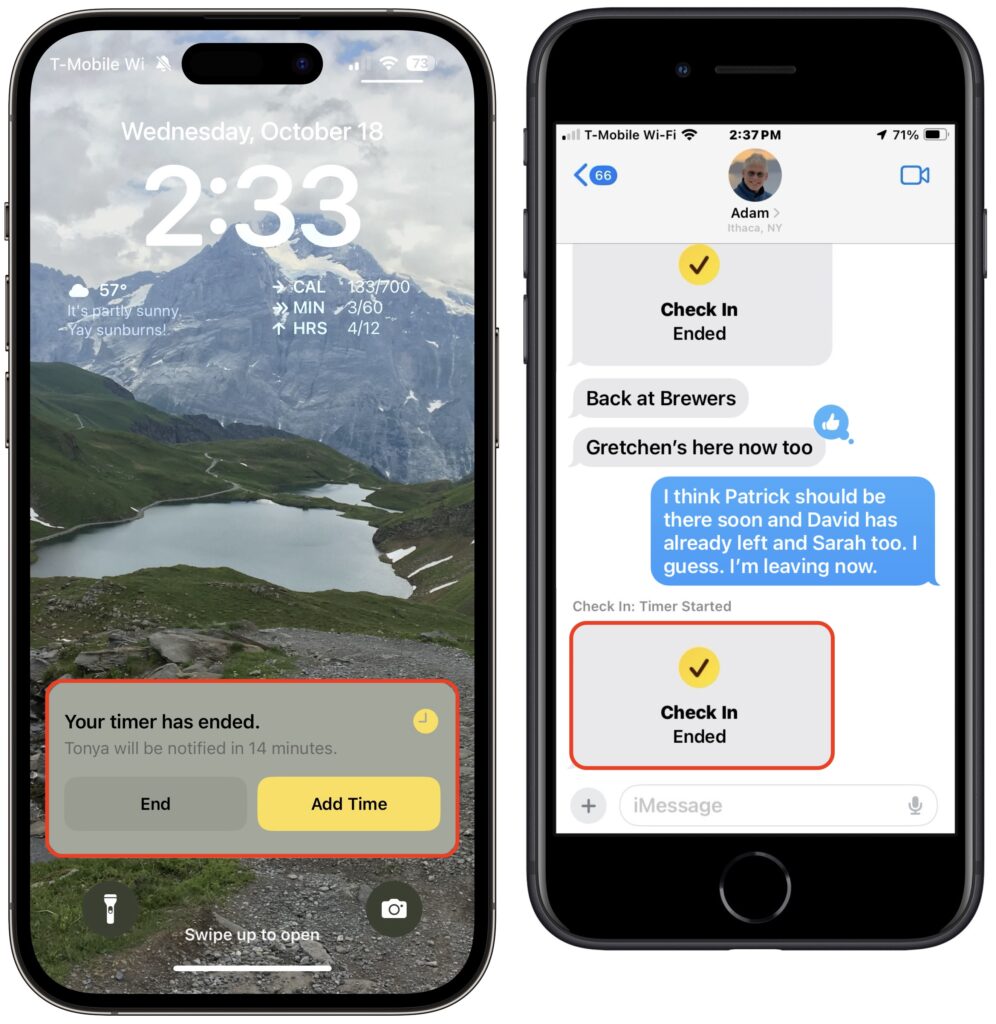
- Check In fails to end (initiator): If you don’t arrive at your destination or fail to tap End when prompted, Check In gives you the option of adding time (below left) but after 15 minutes, tells you that it has alerted your safety partner (below center and right).
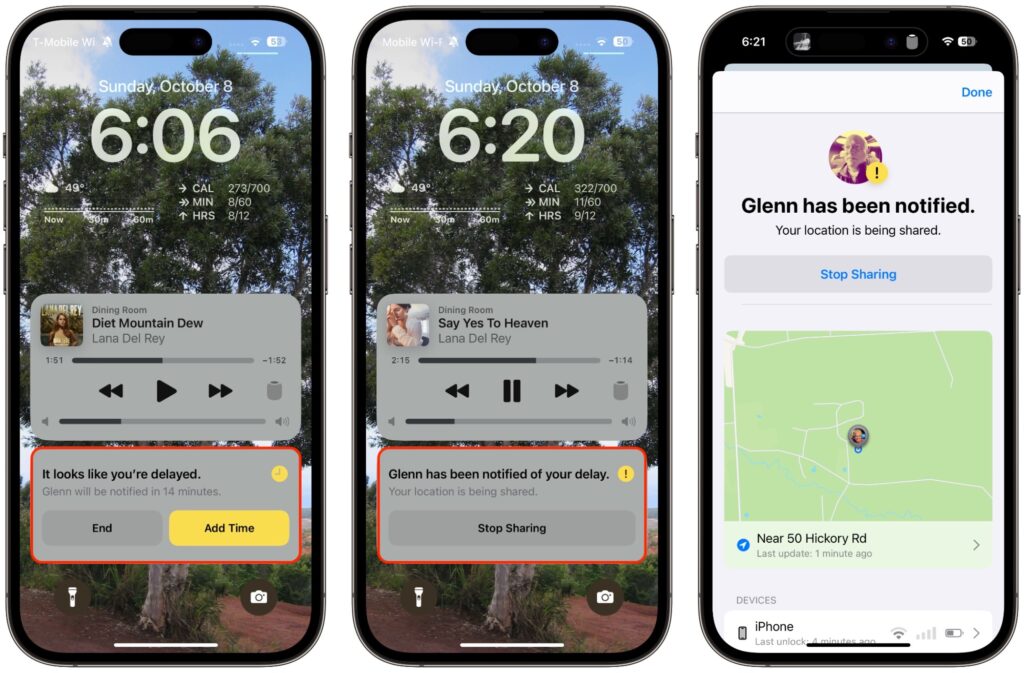
- Check In fails to end (safety partner): More interesting is what your safety partner sees if you fail to complete a Check In. They’ll be alerted and can tap Details to see your location, when your devices were last unlocked, and more. They then have to figure out the best way to respond given your setup conversation.
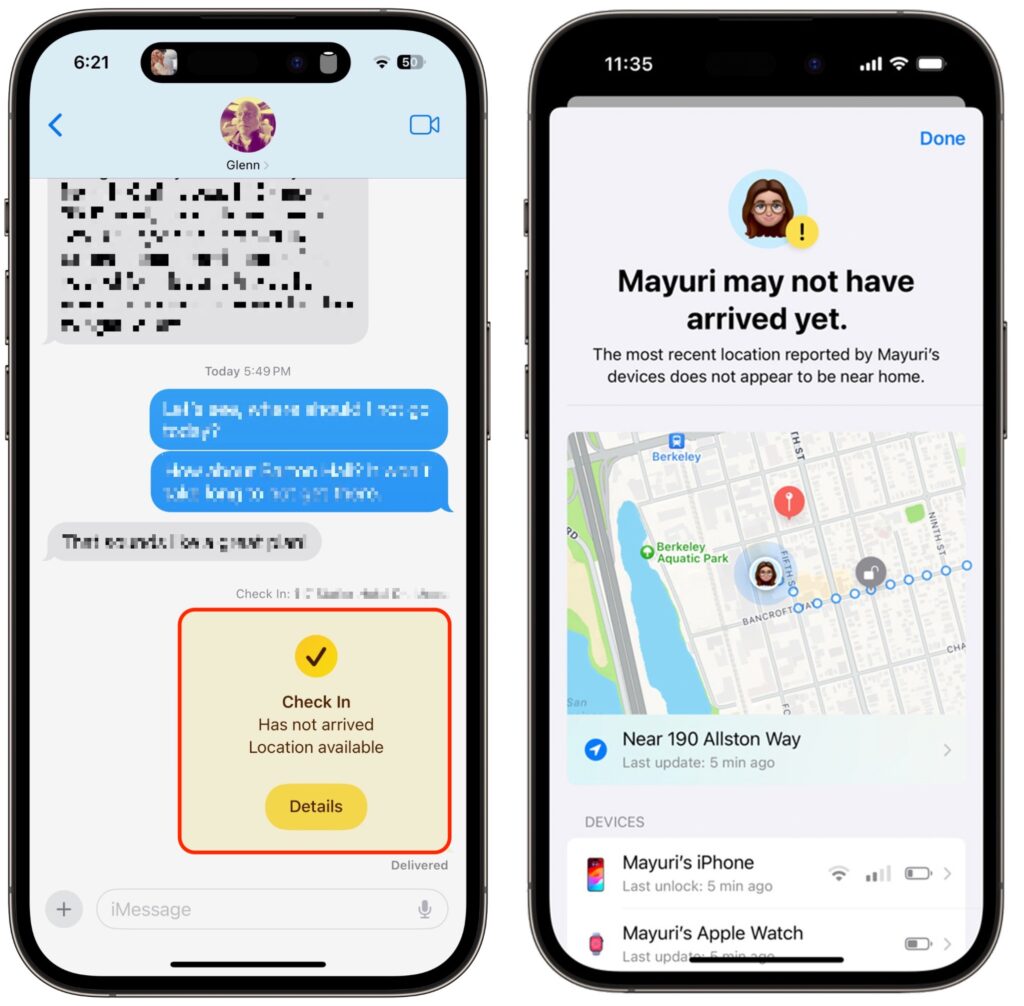
It can take some practice to become fluid with Check In, so it’s worth testing it in everyday situations before using it when it might really matter. Once you use it a few times, you may notice Siri Suggestions offering to start it for you, making it even easier to initiate regularly. We hope you find that it provides some peace of mind and, in the worst-case scenario, helps someone in need of emergency services.
(Featured image by iStock.com/PeopleImages)