Learn How You Can Adjust Web Site Behavior with Safari’s Site-Specific Settings
Although macOS 10.13 High Sierra was light on new features, it did bring one welcome addition to Safari—site-specific settings. Imagine that you regularly visit a blog that you prefer to read using Safari’s Reader view. Rather than invoke it each time you visit, you can now set Safari to use Reader automatically on that site. Similarly, if there’s a site whose text is too small, Safari can remember your page zoom setting for that site. Neat, eh?
Here’s how to make the most of Safari’s site-specific settings. First, load a site whose settings you’d like to customize. Then, choose Safari > Preferences and click Websites in the toolbar. You see a list of general settings in the sidebar at the left, followed by any plug-ins you’ve installed. For each setting or plug-in, you can set what happens when you visit the site you just loaded—or, if you have a bunch of sites open in different tabs, you can customize the behavior for any open site. Here are your options.
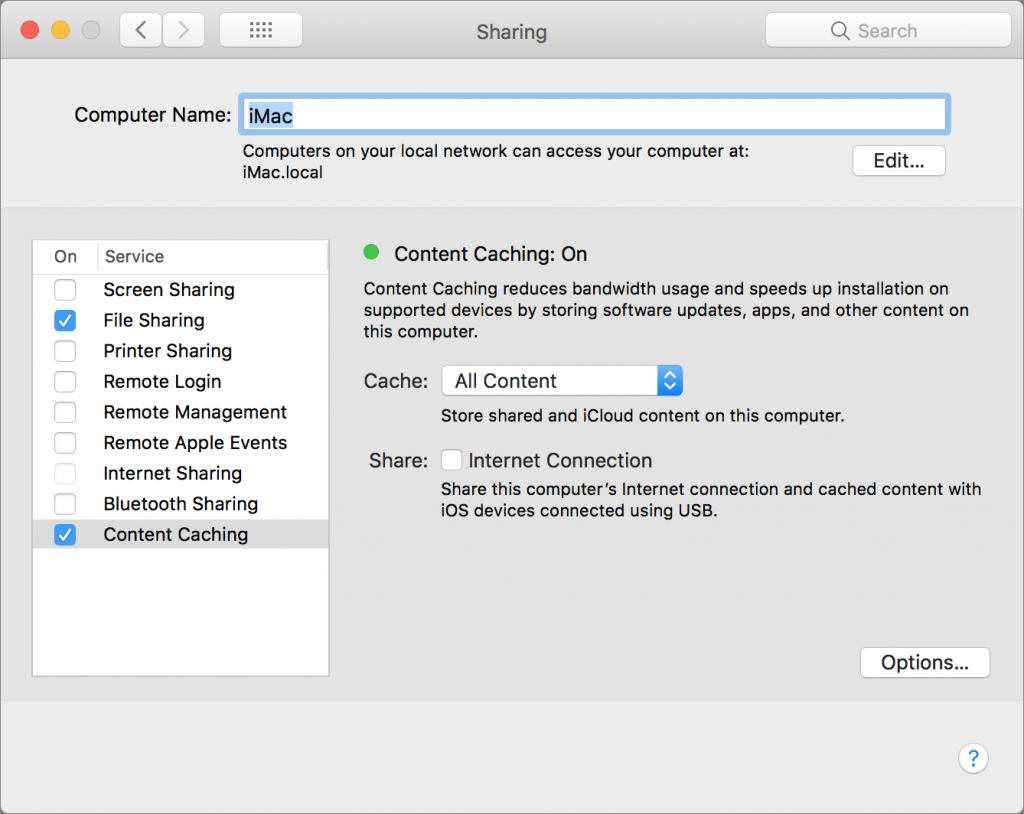
Reader
Reader view displays an article as a single page that’s formatted for easy reading, without ads, navigation, or other distractions. It’s such a significant change that it’s off by default—you enable it by clicking the Reader button to the left of the URL in the address bar. To turn it on for all of a site’s articles, in Safari’s Websites preferences, select Reader and choose On from the pop-up menu next to the site name.
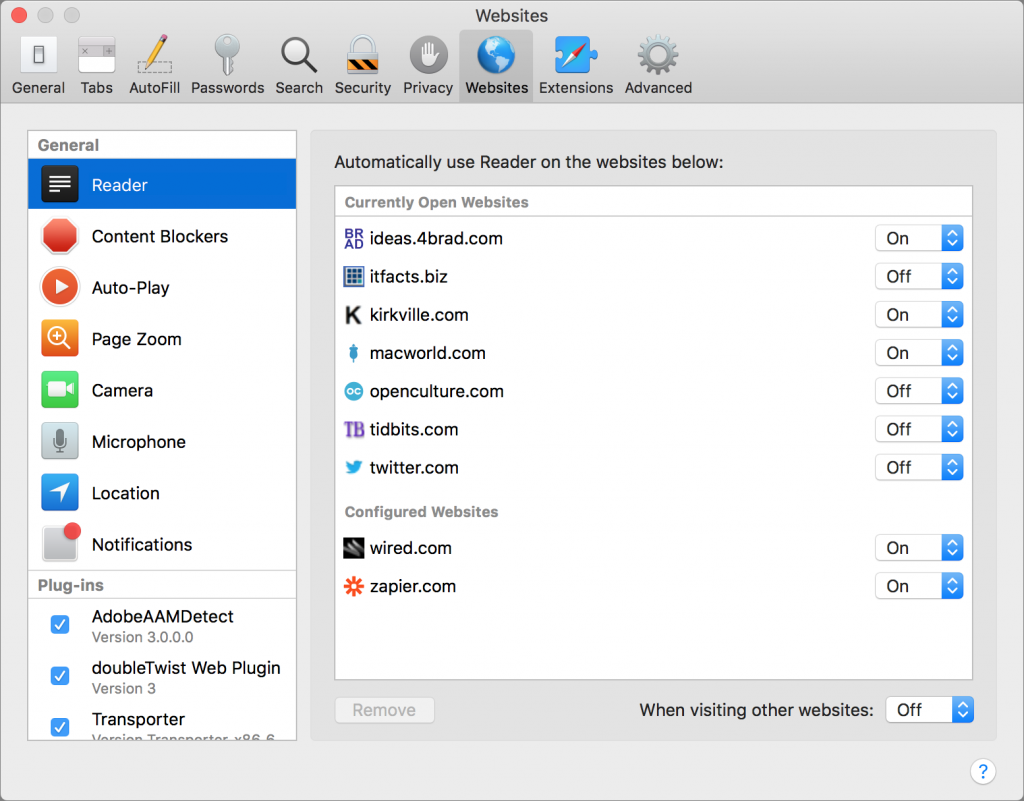
Content Blockers
Another way of seeing fewer Web ads is to install a Safari content blocker. Choose Safari > Safari Extensions to open Safari’s Extension Gallery, and then scroll down slightly to find the page’s Search field, where you can search for blocker. There are lots—look for one like Adguard AdBlocker that supports Safari’s content blocking API. Once you’ve installed one, select Content Blockers in the Websites preferences. By default, Safari blocks ads on all sites, so choose Off from the pop-up menus for sites whose ad content you want to see.
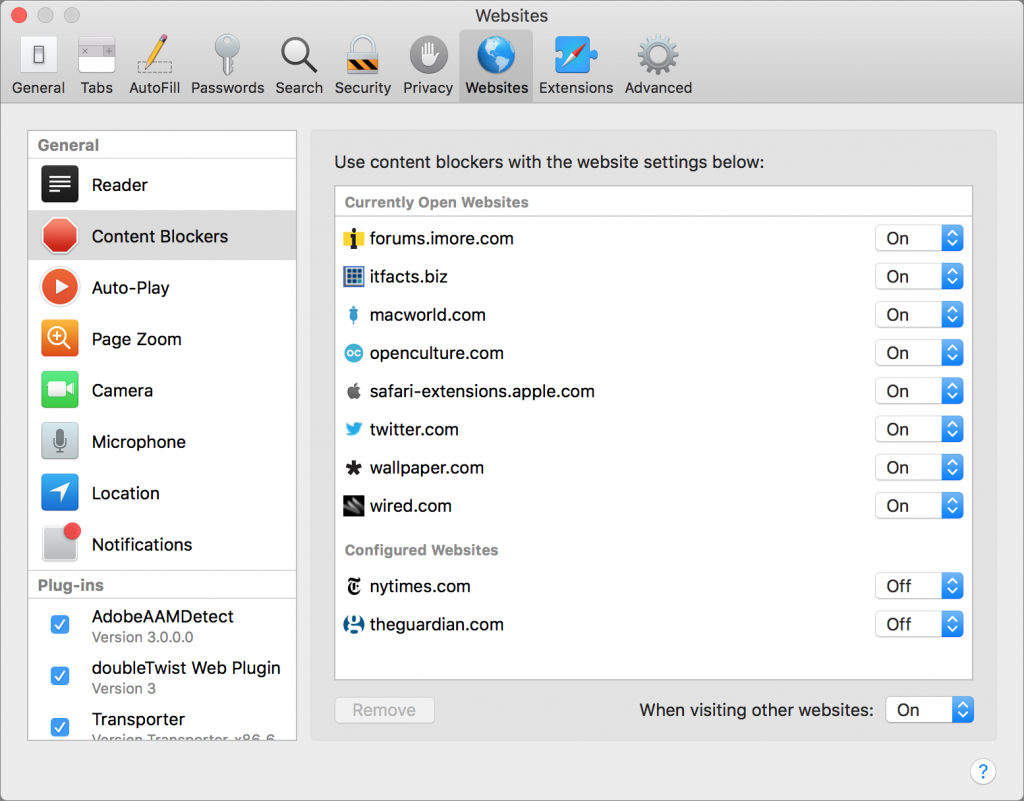
Auto-Play
Little is more annoying than sites that play a video when a page loads, distracting you from the text you want to read. Even worse are those sites—Macworld, we’re looking at you—that auto-play videos that aren’t even related to the page. Safari squelches auto-playing videos by default, but for sites like YouTube, you might want to allow videos to play. You can also choose to stop only videos that have sound.
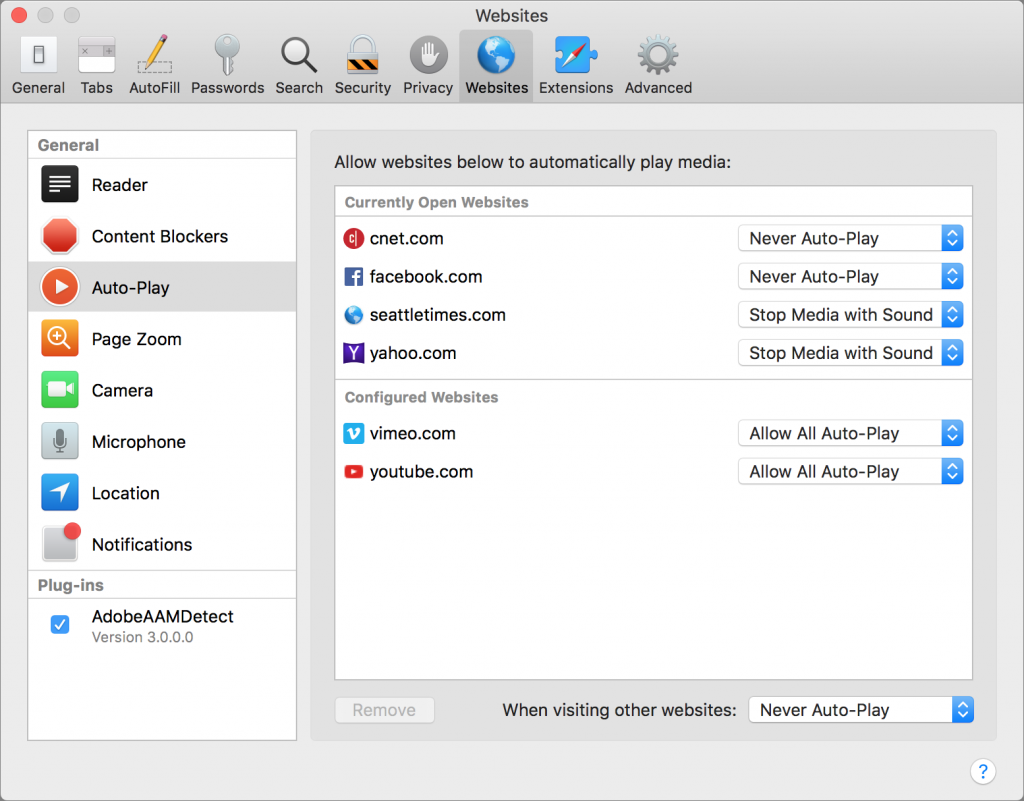
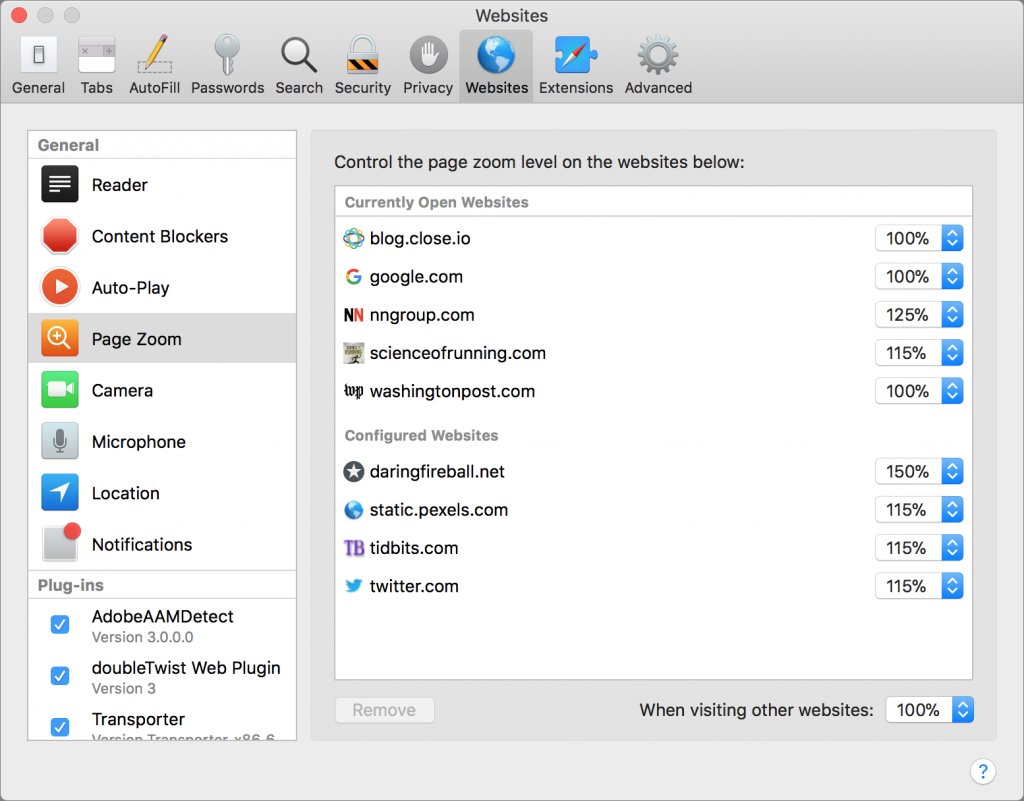
Page Zoom
It’s easy to hit Command-Plus to zoom in on a page, increasing the text and graphics proportionally, but who wants to do that every time you visit a page sporting barely readable words? With the Page Zoom setting, Safari will use your preferred zoom every time you visit a particular site. In fact, you don’t have to do anything other than set a zoom level with Command-Plus when you’re viewing a site because Safari remembers it automatically, as you can see in the Configured Websites section for Page Zoom. To tweak it manually, choose a zoom level from the site’s pop-up menu.
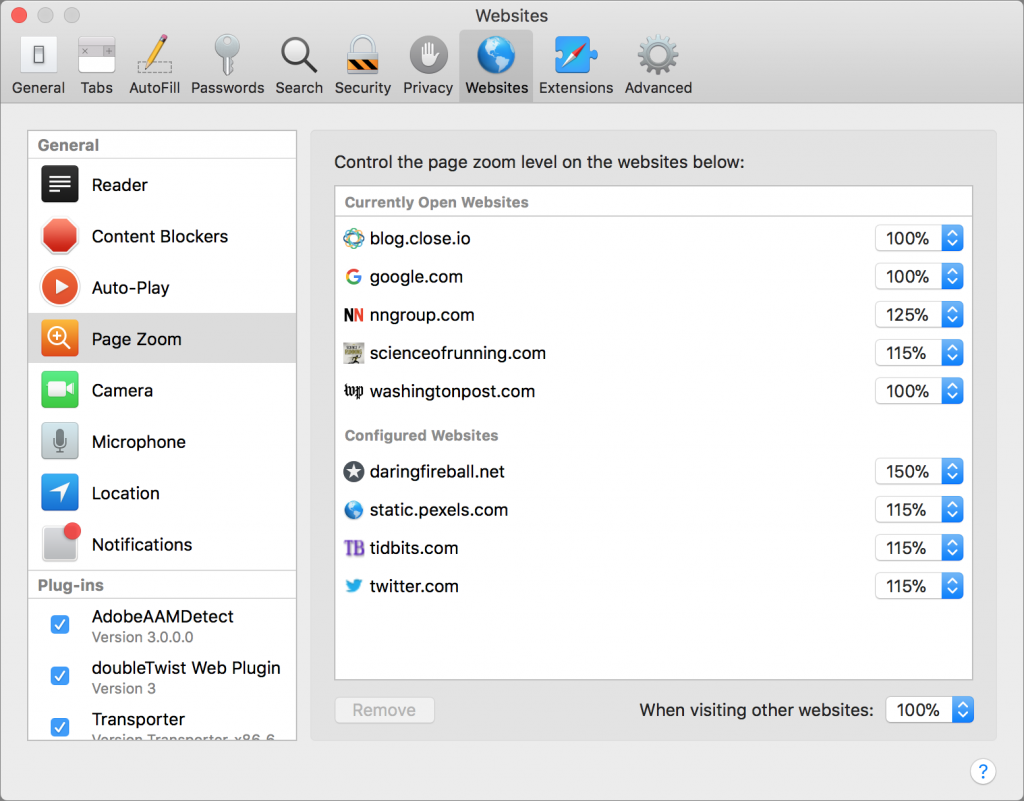
Camera & Microphone
Apart from Web conferencing services, you’re unlikely to run across many sites that want to access your Mac’s camera and microphone. That’s why the Camera and Microphone settings default to asking you whenever a site wants permission to record you. If you find it irritating to be asked constantly by a site you use often, choose Allow from the pop-up menu for that site. And if a site asks repeatedly but you never want to allow it, choose Deny to stop the prompts.
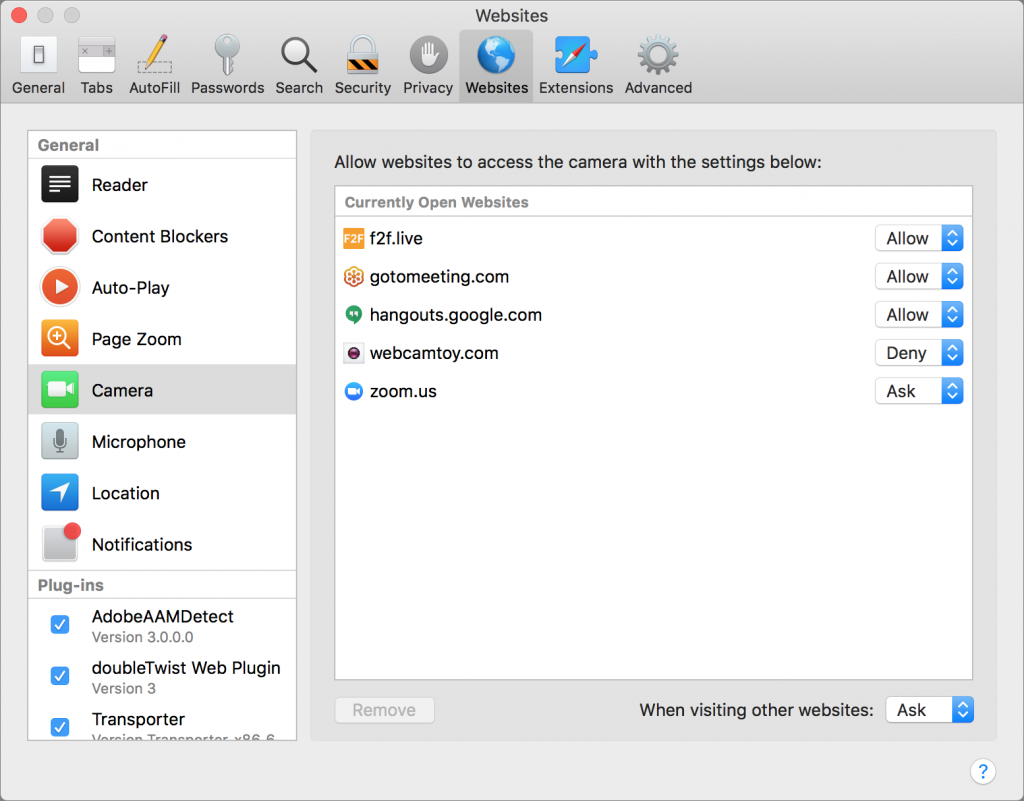
Location
Most Web sites that ask for your location want to determine how close you are to particular stores. If that’s information you’re interested in sharing, let them see where you are, by all means. And if you’re using a mapping service that wants your location, it’s entirely reasonable to set its pop-up menu to Allow. But if a site keeps asking and it feels creepy, set it to Deny.
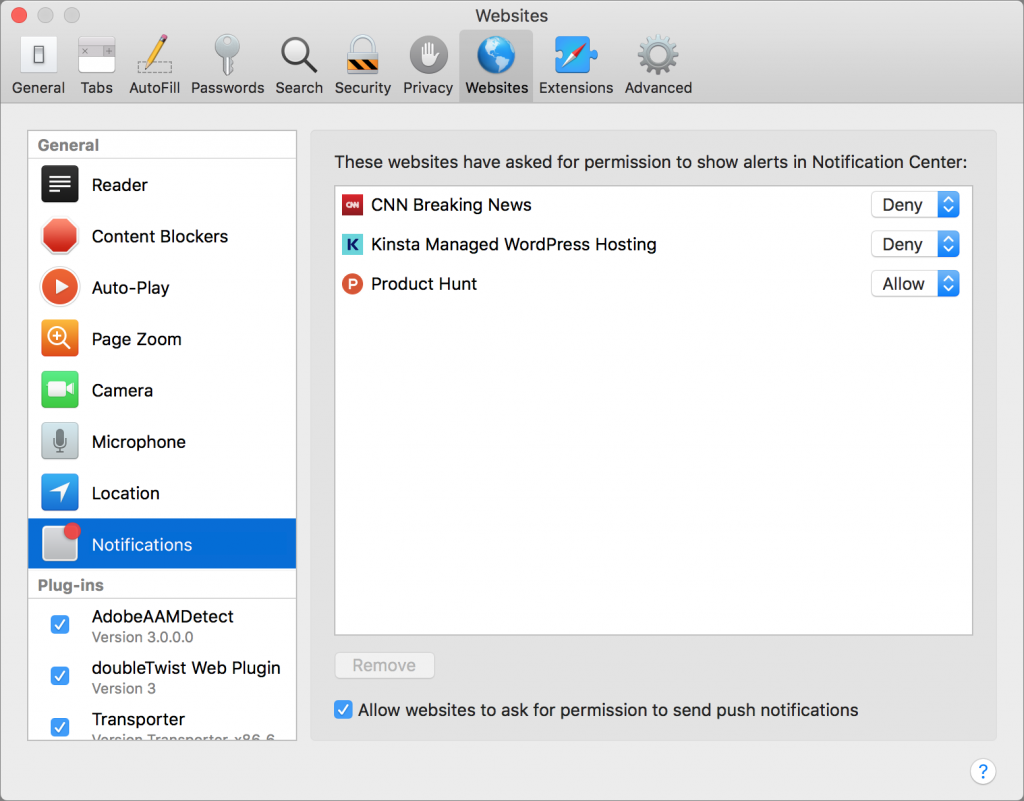
Notifications
Are there sites whose new posts you’d like to know about right away? If they support Web notifications and you give them permission, they can post push notifications that appear on-screen and in Notification Center, just your other notifications.
The Notifications preferences look different from the others because they show only sites that have asked for permission in the past. Safari remembers your choice, and if the site gets annoying later, you can always take back permission by changing the Allow pop-up menu to Deny. And if you never want to be prompted for push notifications—they can be distracting—uncheck the “Allow websites to ask for permission to send push notifications” checkbox at the bottom of the pane.
Plug-ins
It’s impossible to know what plug-ins you’ve installed, but Safari is configured to make sites ask for permission to use a plug-in each time you visit. That’s the safest setting, but for any given site and plug-in, you can use the pop-up menu to give the site access (choose On) or not (choose Off). And if you can’t even remember what a plug-in does, you can deselect its checkbox to disable it.
That’s it! Some of Safari’s site-specific settings work without any interaction from you, such as your page zoom and notification preferences. Others require a tiny bit of configuration, but that’s a small price to pay for the Web working more the way you want.